
New report:
Invalid Click Rate Benchmarks


Click fraud is costing advertisers billions in loses. Learn more here.

Click fraud is costing advertisers billions in loses. Learn more here.
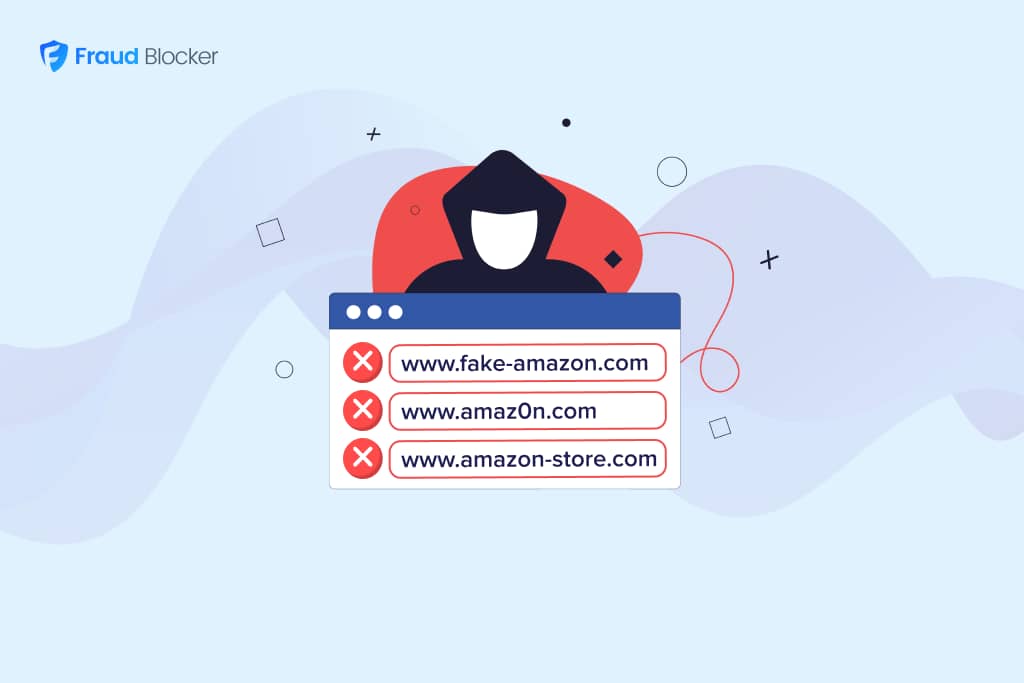

Imagine a customer of yours intends to visit your website, and clicks on an ad that looks exactly like your ad–but with a misspelled URL, which takes them to a page that is a fake clone of your site.
In many industries, this can be devastating: real users can be tricked into giving up sensitive data, including payment information or passwords, and it can harm the reputation of trusted brands in the process. But what is domain spoofing, what does it look like, and how can you prevent it from happening to your business? Let’s dive in.
Domain spoofing is a form of cyber attack where malicious actors create fake websites, emails, or other online entities that appear to be from a legitimate organization.
As mentioned earlier, the goal of these attacks is to deceive users into divulging sensitive information, such as login credentials, credit card numbers, or personal data, which can then be used for fraudulent activities.
You’ve probably heard of the term “phishing”, which is a type of domain spoofing. Other than phishing, domain spoofing happens in a few ways, each posing unique challenges for detection and prevention:
In email spoofing, attackers forge the “From” address in an email to make it appear as though it came from a trusted source.
This form of spoofing is frequently used in phishing attacks, where the recipient is tricked into clicking malicious links or downloading harmful attachments. It may also be used to impersonate high-level executives (CEO or executive fraud), requesting wire transfers or confidential information.
Website spoofing involves creating a fake site that looks and behaves like the legitimate website. These fraudulent sites often feature exact replicas of the design, logos, and content of the targeted organization. Users are lured to these sites via phishing emails, ad campaigns, or social media links, where they unknowingly provide login credentials, personal data, or payment details.
The example above is what’s known as a homograph attack, where attackers register a domain that uses characters that look nearly identical to those of a legitimate domain. As shown, they might replace an “o” with a zero or use characters from different alphabets that appear similar to English letters.
In DNS spoofing, attackers change the address of a legitimate website, redirecting users to a fake version. They do this by “poisoning” the DNS cache, which alters the IP addresses associated with a domain name.
This technique allows attackers to steal personal data or block access to the site altogether, and users are often unaware the attack even occurred, as the fake site may appear and function normally. In other cases, users experience issues when loading the site, and will mistakenly blaming the company for technical problems.
The short answer: Yes!
Domain spoofing not only affects websites and emails, but also impacts digital marketing channels like Google ads, Meta ads (Facebook, Instagram), and other platforms. Here are a few examples by channel, showing domain spoofing affects both advertisers and publishers alike:
Although domain spoofing is often associated with malicious intent, there are rare cases where spoofing occurs for neutral or even non-malicious reasons.
For example, some businesses or organizations may unintentionally create similar domains for localized marketing efforts or franchise differentiation, where the intent is not to deceive but to cater to a specific audience.
Additionally, security researchers may create spoofed domains for ethical hacking purposes, aiming to discover and fix vulnerabilities in a company’s cybersecurity systems.
Now that we’ve covered how domain spoofing occurs, it’s important to learn how to detect when it occurs. Ideally, you take proactive steps to protect yourself. Here are a few ways you can detect domain spoofing:
Once you can detect spoofed domains, taking proactive/preventative measures is the next step. Below are the most effective strategies to guard against domain spoofing:
Domain spoofing, like device spoofing, can be a difficult challenge requiring consistent and proactive steps from businesses and marketers. Hopefully, you’ve found this helpful to understand the techniques used by fraudsters and the importance of comprehensive security strategies.


