NEW New feature: Verify & block fake emails

We improve your ad performance by blocking click fraud and fake emails

Click fraud is costing advertisers billions in loses. Learn more here.

Click fraud is costing advertisers billions in loses. Learn more here.


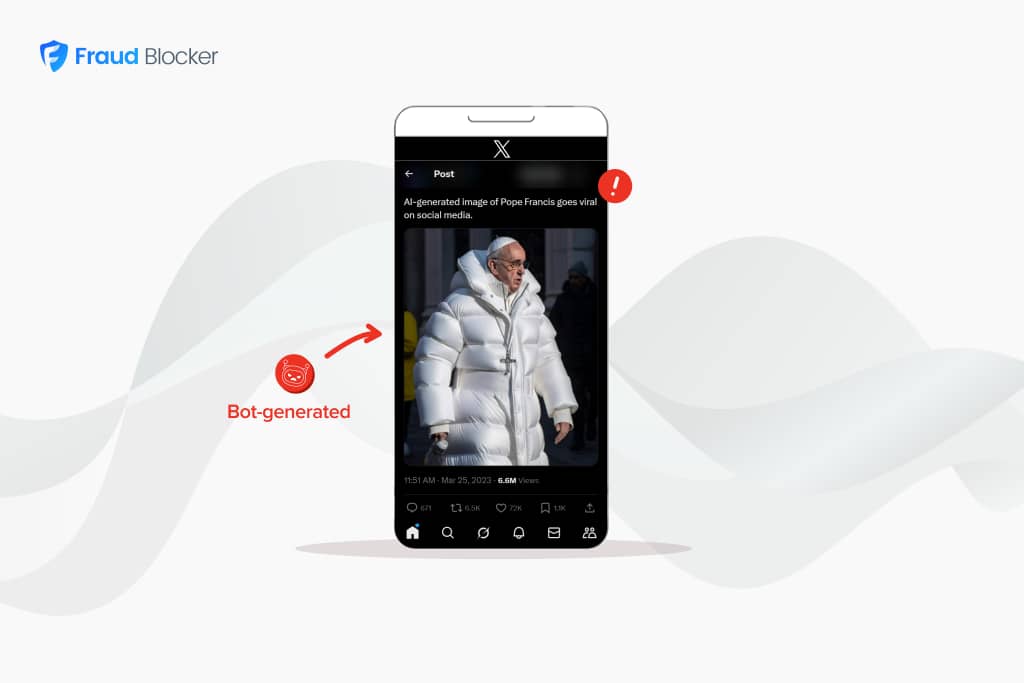
Automated traffic now accounts for the almost half of all internet activity, with reports putting the figure at around 47% in 2023. And while a lot of this automated traffic is doing useful tasks, such as collecting the data we rely on, or carrying out repetitive tasks, there is also plenty of murky and more malicious bot traffic out there too.
Botnets are often one of the more insidious forms of fake traffic online. But what exactly is a botnet? Are botnet attacks something you need to be worried about? And how can you spot botnet activity on your online ads?
With nearly half of all internet traffic being non-human, it helps to understand what this actually means. There are good bots, and bad bots.
A study by Imperva indicates that good bots account for a sizable portion of this traffic, but bad bots make up around 32% of bot activity online.
A quick explainer:
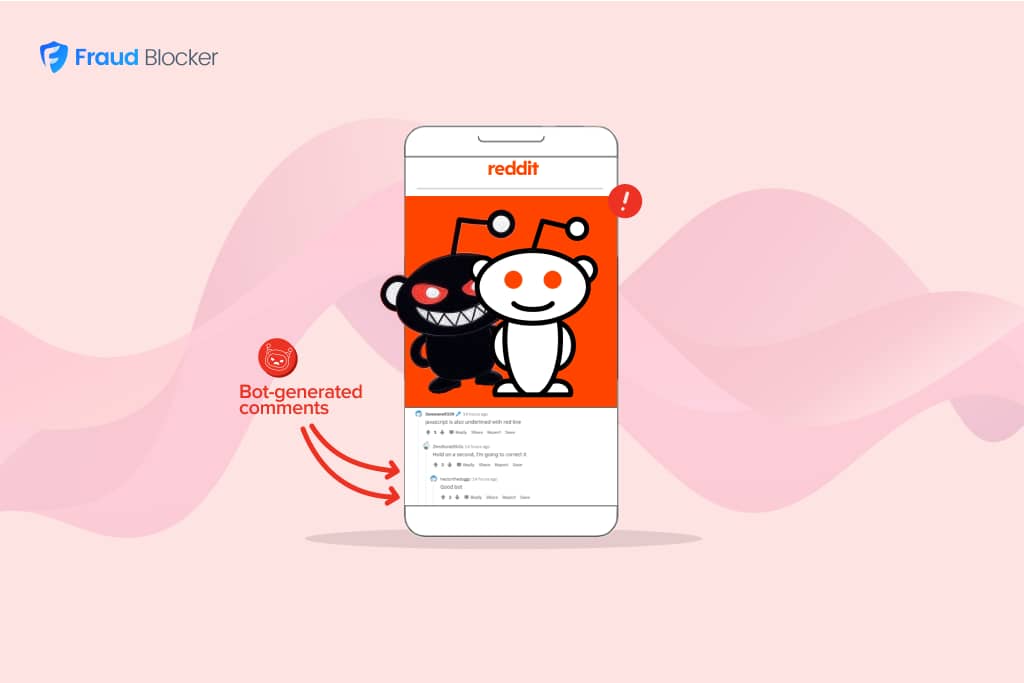
If you run or manage a website you will definitely experience some form of bot based activity, the most common being spam emails or spam comments.
Spammers and fraudsters often leverage the power of botnets to carry out their dirty work. These huge networks of connected devices infected with malware can be hired for very little money, or even accessed – if you know what you’re doing.
A botnet is a collection of internet-connected devices, which could include computers, servers, mobile devices, or IoT devices. The common theme is that they have all been infected by malware and brought under the control of a single attacking party often known as the “bot-herder.”
These individual devices, known as “bots,” are commanded to execute tasks en masse without their owners’ knowledge or consent.
Malware infections will often enter a device via the following methods:
Once malware is installed, the bot-herder can remotely direct these devices to perform coordinated functions. Think of it like a nefarious puppet master pulling on digital strings.
The rate of infection and the growing complexity of these networks signify an alarming trend. It is not just the sheer size but also the sophistication of modern botnets that pose a grave threat to the integrity of internet traffic.
Botnets are as versatile as they are rampant. Many botnets are designed for specific purposes, such as the tasks below. But they can easily be adapted to carry out any form of cyber attacks, even if that wasn’t their original purpose.
Some of the most common uses for botnet malware includes:
The versatility of botnets ensures they are a preferred tool for cybercriminals, enabling large scale scams, fraud-as-a-service setups, and attacks with a veil of anonymity.
Click fraud, or ad fraud, are some of the most popular uses for botnet attacks. The reason being that they are some of the most lucrative and relatively easy forms of cyber crime.
In fact, the Cost of Ad Fraud report from Juniper Research found that $84 billion was lost to ad fraud globally in 2023.
With ad fraud campaigns such as Methbot, the bot herders simply set up their fake websites and then direct massive amounts of fake traffic to interact with the paid content. There are often sophisticated processes to hide the true nature of this traffic, such as using VPNs or hiding in infected machines and hijacking genuine user activity.
Ad fraud bot campaigns cause damage well into the millions of dollars. And while the headline grabbing campaigns of Methbot, 3ve and Drainerbot are well covered, there are many more fraudulent campaigns running that are costing advertisers less shocking dollar values. But of course, just because they aren’t making headlines, doesn’t mean they aren’t sapping budgets.
Read more: The biggest ad fraud scams.
One of the most insidious uses of botnets is ad fraud, a deceptive practice undermining the integrity of Pay-Per-Click (PPC) advertising campaigns. While the ad platforms such as Google and Meta do offer protection (and apparently sophisticated detection mechanisms) relying on the in-house bot detection doesn’t always work.
This is because bots are becoming increasingly adept at imitating human behavior and slipping under the radar. And, in addition to this, the ad platforms such as Google are less likely to exclude traffic that isn’t overtly bot based.
The responsibility is increasingly on the advertiser to track and block bot activity.
Here are some signs that might suggest the presence of bot activity in PPC ads:
Read more: Click fraud vs invalid traffic?
While it is unlikely that the average business will be the target of a botnet attack, it is important to have an effective solution in place to blocking fraudulent traffic (including botnet attacks) on your PPC ads.
Find out why pro marketers are increasingly turning to Fraud Blocker. Try us out and block bad traffic on your Google and Meta ads with a 7 day free trial.