NEW New feature: Verify & block fake emails

We improve your ad performance by blocking click fraud and fake emails

Click fraud is costing advertisers billions in loses. Learn more here.

Click fraud is costing advertisers billions in loses. Learn more here.

Imagine waking up to discover thousands of fraudulent transactions on your site. Your payment processor has suspended your account, and customers can’t check out. Your business reputation is taking a nosedive, and you have no idea what’s happening.
This isn’t a worst-case scenario—it’s exactly what could happen if a carding attack hits.
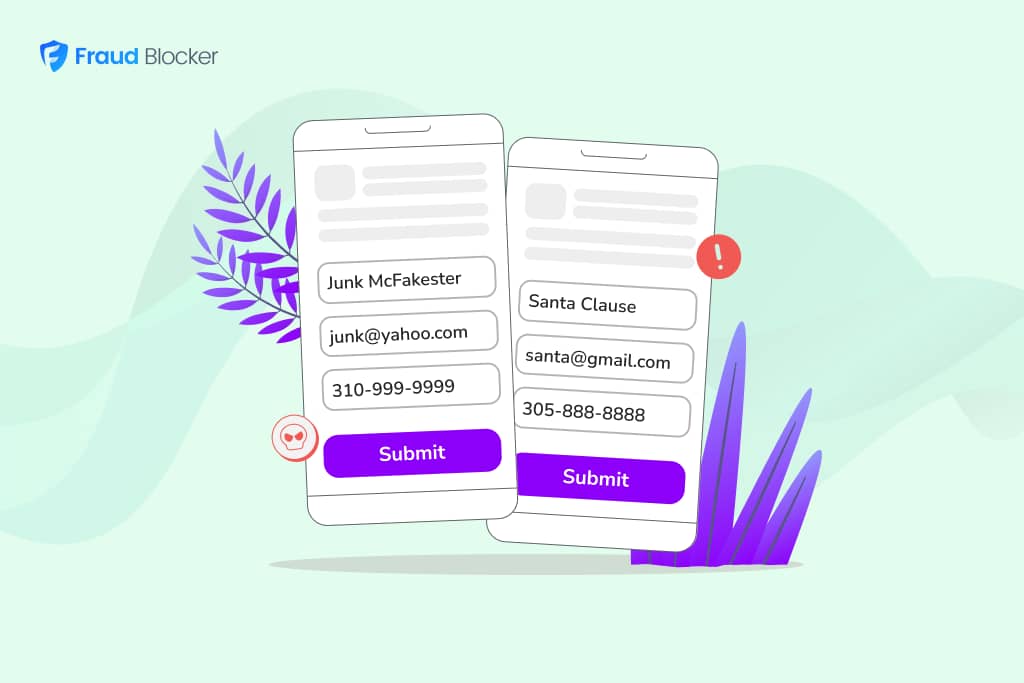
We should know! We deal with carding attacks all the time. Sometimes, dozens of attempts, every day for months. See below:
And it’s not just Fraud Blocker. According to Finances Online, carding attacks have tripled over the past 10 years as card testers become more sophisticated and persistent. Your business could be next.
However, it’s possible to protect your business. In this post, we’ll share the most effective strategies we’ve used to defend against carding attacks. But first…
A carding attack is a cybercrime in which fraudsters try to complete transactions with several stolen credit card details, to verify which ones are active and can be used for larger fraudulent purchases.
These are also called card testing attacks, and they usually target businesses with high transaction volumes and minimal security measures, such as small-business ecommerce platforms and subscription services. Non-profits and donation sites are also high susceptible to spam donations and carding attacks.
Here’s how a carding attack typically works:
These attacks can go unnoticed for hours or even days, and when businesses discover them, it’s too late.
The problem with card testing attacks isn’t just fraudulent charges. Small, low-value transactions accumulate and can eventually burden your payment processes and overall infrastructure.
Here are some specific dangers to be aware of:
Every transaction, even a failed one, can cost your business money. Carding attacks often generate hundreds or thousands of failed payment attempts, which can inflate costs and cut into margins.
If even one of these fraudulent transactions slips through, the card owner can charge it back. Multiple chargebacks lead to penalties, higher processing fees, or even termination of your merchant account.
Too many card attempts can trigger fraud prevention measures, blocking legitimate transactions. If your payment provider blocks transactions, legitimate customers can’t check out, which means abandoned carts. Since only about 38% of customers return to try again, that’s a lot of lost revenue.
At Fraud Blocker, we’ve tried several strategies to stop these carding attacks without disrupting the user experience. Here are the six most effective solutions we discovered:
Cloudflare firewall protection and other Web Application Firewalls (WAF) can form a layer of security, blocking carding bots and malicious traffic before they reach your website. They can filter requests based on IP reputation, geolocation, and known attack signatures to ensure that your site’s resources only serve real users. This makes them a powerful option for stopping card testers.
Carding attacks use bots with similar behavior to those used in ad fraud. That makes ad fraud prevention tools like Fraud Blocker and similar platforms an excellent solution. Our system looks for unusual behavior like multiple requests from a single IP address or suspicious referrer sources, we identify those sources (which are usually bots), and prevent them from interacting with your website.
Stripe Radar is another highly effective fraud prevention system integrated with the Stripe payment gateway (your payment gateway may have a similar fraud prevention system). It uses machine learning to identify suspicious transactions in real time and uses features like custom rules and dynamic scoring to set tighter transaction restrictions. Its systems are so effective that Stripe Radar blocked 16 million fraudulent transactions during Black Friday weekend alone in 2023.
Requiring details like the CVV, postal code, and billing address attached to a credit card adds friction for attackers who lack this information. And while reducing the number of matching requirements can marginally speed up customer checkout, the extra step can be a net positive for your business because you reduce the risks of failed customer transactions due to blocked payment gateways.
Email verifications are another way to add friction for carding bots since they often can’t access valid email boxes to confirm an account. Additionally, verification tools like ZeroBounce can validate email addresses, automatically block fake or invalid addresses during a carding attack, and let real users through.
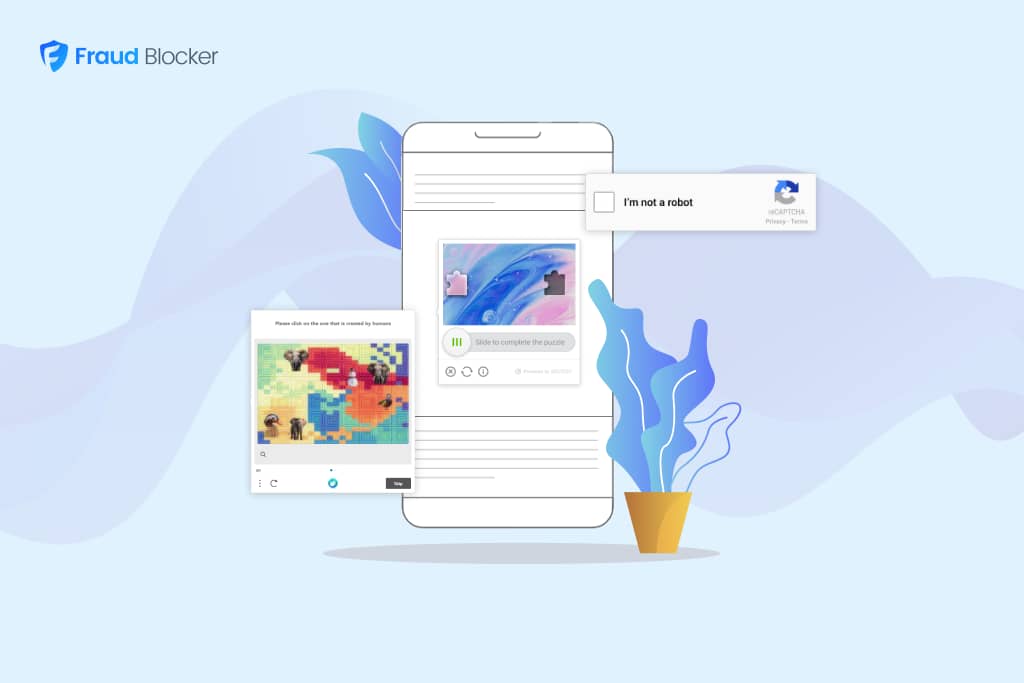
CAPTCHA remains one of the easiest ways to keep bots off your website. However, they can inconvenience real users and work against your efforts to increase conversion rates. A recent study on the checkout experience found 29% of real users fail CAPTCHAs.
This is why we recommend that your business explore other options before implementing CAPTCHA. It’s also important to note that CAPTCHAs aren’t a perfect solution, as a study on ARXIV.org shows that some bots can solve them 100% of the time.
If left unchecked, carding attacks can drive up costs and threaten your business’ operational stability.
But it doesn’t have to end that way. By monitoring your metrics and implementing the strategies we’ve outlined, you can build a robust defense against these attacks. At Fraud Blocker, we’ve seen the devastating impact of carding attacks firsthand—and we’ve also seen the difference proactive measures can make.
Fraud Blocker can protect your website and campaigns from unusual activity by analyzing and blocking suspicious traffic. Try our 7-day free trial to protect your campaigns and improve your ad performance.